PackNet Software Platform Security Guide
PackNet Software Platform Security Guide
Purpose
This document will cover a description of the security controls for the PackNet Software Platform solution and provide a high-level overview of the Packsize Security Program. This document is intended to be shared with potential and existing customers.
Introduction
Building trust with customer partners is a top priority of Packsize. We understand our responsibility when customers entrust us with the secure data that is required to support a right-sized packaging solution.
To maintain customer confidence in our security posture and in the security features we provide, we work diligently to continuously improve security processes and controls and provide our customers with the right features to secure data.
Packsize takes security seriously by continuously improving security posture and allowing customers to do the same. By providing a detailed understanding of the PackNet Software Platform security controls and features, Packsize strives to convey the depth of commitment to customer confidentiality and privacy.
PackNet Software Platform Solution Overview
PackNet Software Platform supports a variety of automated solutions for on-demand right-sized packaging. This includes automatically dimensioning products at induction, cutting right-sized corrugated, wrapping the corrugated around the product, fully sealing the box, and labeling it on outbound with a shipping label.
The PackNet Software Platform is a cloud-based multi-tenant software solution. It offers standard integrations to customers and provides real-time analytics and data insights to help them make informed decisions about their packaging processes. This solution enables a seamless connection between customer warehouse management systems and queuing systems that support custom fulfillment processes. As a cloud-based software, PackNet Software Platform is designed to scale dynamically to processing demands and machine implementations per customer.
PackNet Software Platform High Level Architecture and Process
PackNet Software Platform is hosted in the cloud and interacts with an IoT edge device through secure encrypted channels. The IoT device, which is located within the machine at a customer site, interacts with the control system and accessories that support the right-sized packaging solution.
For more detailed information around the solution and integration points, refer to PackNet Integration Requirements.
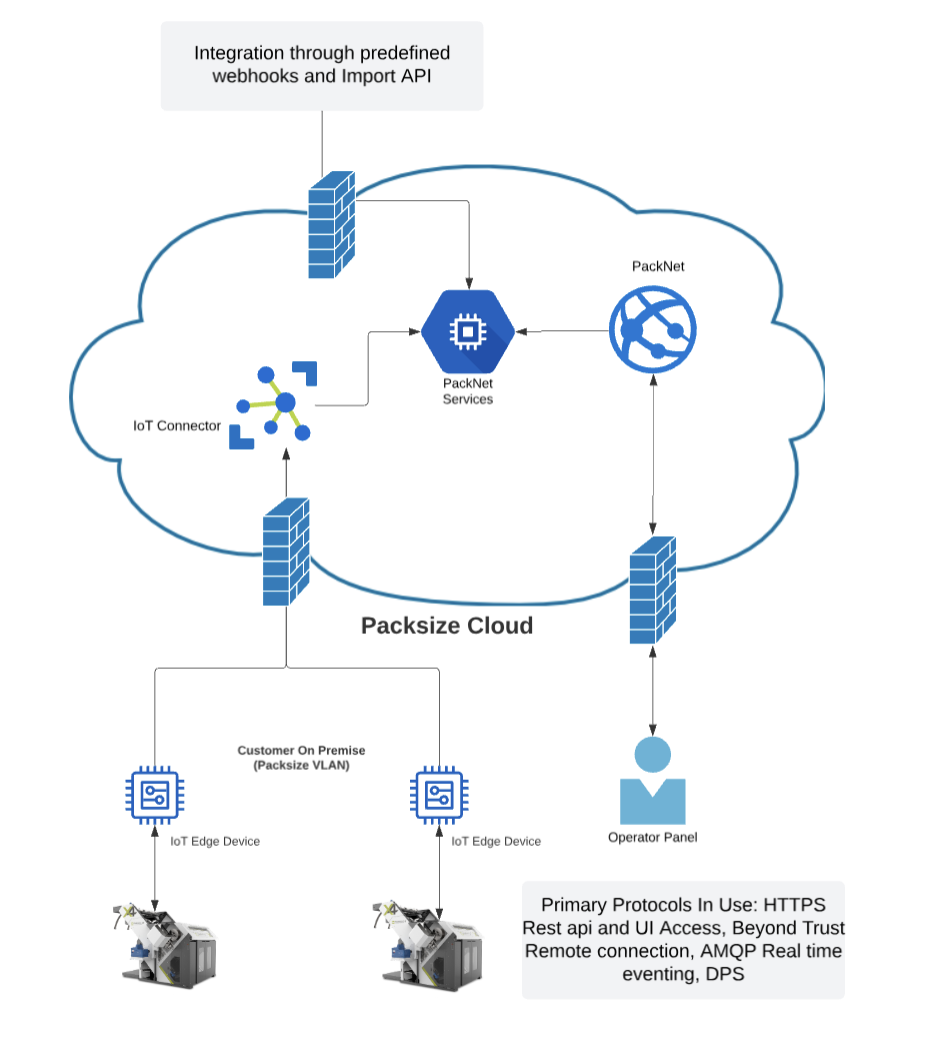 |
Ingest
Customers will send data to PackNet Software Platform hosted application through predefined integrations. The integration communicates to the PackNet Azure Cloud environment over an encrypted channel.
Process and Prioritization
PackNet processes the job data and decides staging and production based on customer priority configuration. Once a machine has been selected to produce the packaging solution, the information will be sent in an encrypted format to the IoT device of the selected machine.
Produce
The IoT device will send data to the Programmable Logic Controller (PLC). The PLC may send data to other accessories that are needed to support the solution. At this point the Packsize machine will create a custom right-sized packaging solution for that specific order.
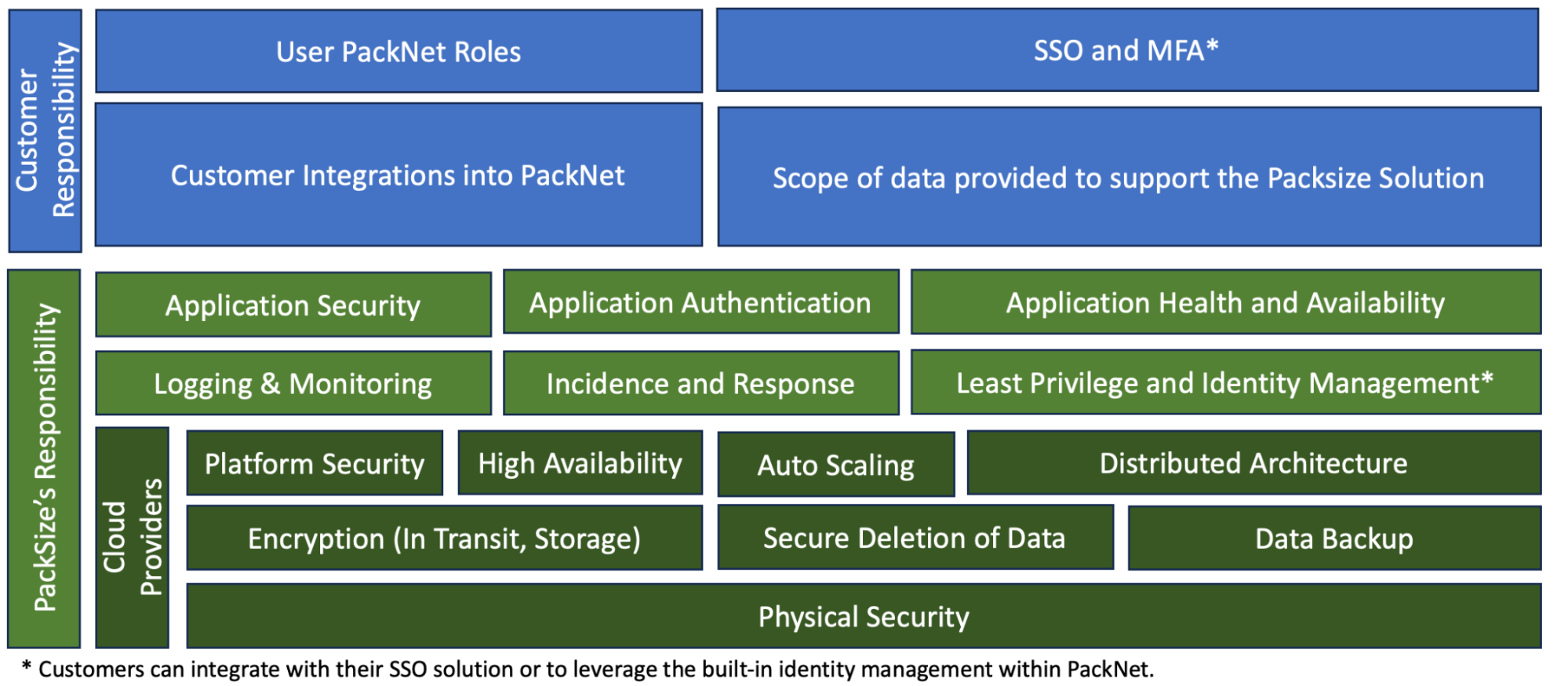
Data in Scope
It is the responsibility of the customer to determine the type and volume of data that is required to support the Packsize solution, data requirements vary greatly across solutions. Packsize will protect the data that flows through as outlined in the following sections.
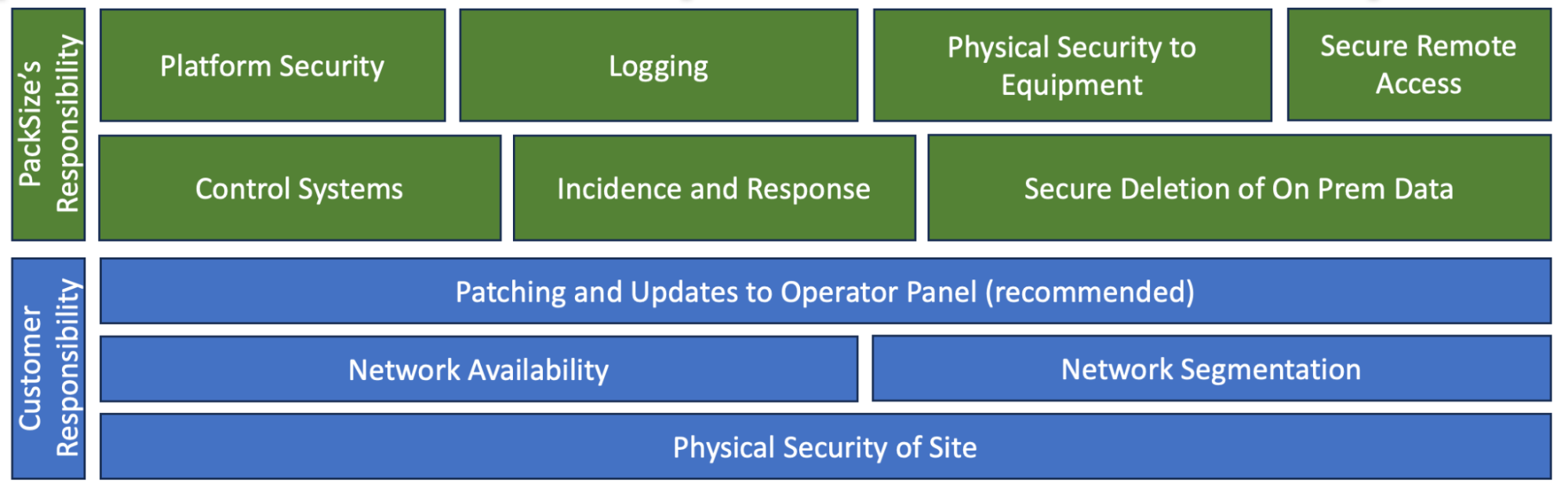
Machine Specifications and On-Premise Controls
The controls around encryption and data retention vary depending on the solution and supporting technology. Refer to the machine-specific Packsize security standard for details around the specific technology and software that will support the solution and the related data controls.
Many of the control systems and vendor appliances do not allow for encryption in transit or in storage. Because of this, mitigating controls are recommended to limit access to the data that is unencrypted in transit. See Packsize Recommendations to Protect On-Premise Data.
PackNet Software Platform Controls
Authentication and Authorization
PackNet Software Platform supports multiple authentication and authorization methods which gives customers the flexibility to meet their individual requirements and needs.
If purchased as part of the solution, customers can use standard SSO integration with PackNet Software Platform via Oauth2 and SAML2. This allows customers to leverage access controls embedded in their SSO solution, which could include account lockout, password complexity, password history, multi-factor authentication, etc.
Packsize provides customers with the capability to manage their users and administrators and allows granular access control capabilities through user permissions. Within the authentication process, PackNet Software Platform has controls that require password complexity. When a user sets their password in PackNet Software Platform, it is processed by a one-way hash function, also known as a message digest, in which an algorithm takes the password string and converts it into a fixed-length binary sequence that is computationally difficult to invert. Only the one-way hash of the password is stored within the application. Users can reset their password at any time.
System components are configured such that the organization and its customers' access is appropriately segmented from other tenant users.
Encryption
All data transmitted between PackNet Software Platform environments and Packsize customers is protected by Transport Layer Security (TLS), which is enabled by default and cannot be disabled. Communication between PackNet Software Platform and IoT edge device requires TLS 1.2 encryption and a minimum key length of 64 bits for the initial connection. Subsequent traffic is encrypted with a 2048 bit certificate. For integration points, TLS 1.3 is required for encryption of data flowing into the PackNet Software Platform environment.
Encryption at rest serves as a safeguard, ensuring that any stored files or data can only be accessed by an authorized process or application through decryption. Encryption for data at rest is automated using Azure’s transparent disk encryption, which uses industry-standard AES-256 encryption to secure all volume (disk) data. All keys are fully managed by Azure. (See Azure Transparent Encryption.)
PackNet Software Platform leverages Atlas Mongo DB for cloud data storage to support the PackNet Software Platform solution. Customer data is encrypted at rest by default using AES-256 to secure all volume (disk) data. The process is automated by the transparent disk encryption of the customer's selected cloud provider, and the cloud provider fully manages the encryption keys. (See Atlas Mongo DB Encryption.)
Data Storage and Deletion
Job production data that is stored in a cloud environment is encrypted at rest by our cloud vendors. This data is available for 30 days in order to triage jobs that have been sent to the PackNet Software Platform environment. Following this time period, the data is automatically removed through a secure deletion process. Depending on the timing of backup snapshots, the data may be retained within MongoDB backup for one year if the snapshot was taken before the auto-delete. This data retention period may be shortened by adjusting the settings in Secure Print.
Packsize captures metadata around quality and efficiency to support PackNet reporting which provides metrics and dashboards for customers. This data is captured and stored in an encrypted format indefinitely.
Malware Protection
Anti-malware agents are installed within the control panel to scan all files in real time for known and unknown threats. Behavior analysis is in place to detect and block suspicious activity on endpoints, and alerting is in place for the security operations team to triage and investigate the suspicious activity.
Security software (including firewall, anti-virus, and anti spam) is installed and enabled on company laptops and workstations. Disk encryption is enabled across company workstations.
Firewall
All traffic to the cloud environment is filtered and routed to specific endpoints. Azure Front Door will block all other traffic to the cloud environment. The network filtering integrates with Azure security monitoring and logging ecosystems which can provide real time insights to detect and mitigate against potential threats.
Logging and Alerting
Packsize maintains a centralized log management system that gathers, stores, and analyzes log data, serving various purposes such as health monitoring, troubleshooting, and security. Additionally, the system is equipped with configured alerts to promptly notify Packsize Site Reliability Engineers (SREs) about any operational issues that may arise. Leveraging these insights, Packsize teams can provide optimal support for customers.
Secure Remote Access
Packsize only uses remote access technology in order to provide support and address any possible issues within the Operational Technology environment. Packsize only uses remote access technology that provides sufficient safeguards for traffic encryption (TLS 1.2, AES) with RBAC.
IoT Security and Device Provisioning
Packsize leverages the IoT Hub Device Provisioning Service (DPS) to facilitate secure, zero-touch, just-in-time provisioning of IoT edge modules to the appropriate IoT hub eliminating the need for human intervention. Utilizing TPM hardware-based security features, Packsize ensures robust device authentication and platform integrity by registering IoT edge modules public keys or endorsement keys with Azure DPS enabling secure recognition and provisioning of devices upon boot-up. See DPS Overview for more details on the DPS provisioning process.
Monitoring of Threats Incident Response
Logs from the cloud environment and control panel are gathered in a Security Information and Event Management (SIEM) solution. The SIEM is monitored 24/7/365 to detect potential threats and to direct actions to manage the impact and resolution of a security incident.
Packsize will maintain an incident response plan and follow documented incident response policies including data breach notification to the Data Controller without undue delay when a breach is known, or reasonably suspected, to affect Client Personal Data.
Physical Security
Packsize implementations will include a locked, tamper-resistant cabinet which will prevent unauthorized access to sensitive equipment and data. Access to the lock's key or combination is restricted to authorized Packsize personnel based on least privilege.
Resiliency Controls
Packsize has taken great care to select cloud partners who can provide and host a reliable solution. See table below for current SLAs and links to resiliency control documentation provided by Packsize's cloud providers.
Cloud Vendor | SLA | Additional Information |
|---|---|---|
Azure | 99.95% | |
Cloud AMQP | 99.95% | |
Atlas MongoDB | 99.995% |
Incremental backups are performed daily using an automated system and replicated to an offsite location. Backups are monitored for failure using an automated system.
Packsize Security Program
Packsize maintains an Information Security Program that establishes robust administrative, technical, and physical safeguards to protect customer data and ensures the capability to identify, detect, respond to, and recover from security incidents effectively.
Application Security
Regular reviews are conducted through PackNet Software Platform by both internal and external security teams. Internally, the platform undergoes periodic risk assessments, and threat modeling which involve technical vulnerability discovery and evaluation of business risks and concerns. Third parties are engaged on a regular basis to conduct application penetration tests and cloud security reviews.
Software Development – Best Practices
Packsize Information Security and PackNet Software Platform product teams work proactively together on security initiatives in the SLDC. Packsize has implemented tooling and practices to ensure operational security within the PackNet Software Platform. We leverage third-party security tools to conduct source code scans, detecting and addressing known security vulnerabilities and preventing unsecure code from being pushed to production. Additionally, we test our code against government benchmarks, including Common Vulnerability and Exposure (CVE) and Common Weakness Enumeration (CWE).
Packsize has an established formal change management process. This is to ensure that the proposed changes are reviewed, authorized, tested, implemented, and released in a controlled manner, and that the status of each proposed change is monitored.
Development and test environments are separate from production environments with access control in place to enforce separation. Duties shall be separated between personnel assigned to the development and test environments and those assigned to the production environments.
Security Updates and Patch Management
Packsize will maintain the Operational Technology (OT) environment by applying updates recommended by vendors on a consistent basis. If critical security updates are identified, Packsize will notify the customer to coordinate downtime to apply the fix.
Identity Management and Least Privilege
In general, Packsize personnel do not have access to customer production data. Only a small group of privileged users have the authority to access production infrastructure.
Packsize adheres to the principle of "least privilege" for these users, ensuring that access is limited to the minimum scope necessary for resolving the critical issue. The access process for privileged users requires MFA. Additionally, Packsize revokes a privileged user's access when leaving the company.
Risk Management and Governance
Packsize is continuously monitoring, auditing, and improving the design and operating effectiveness of all security controls. These activities are regularly performed by both third-party credentialed assessors and Packsize internal teams.
The Packsize Information Security Director and Security team are responsible for the implementation and management of our security program. The Security Director is supported by the product security partners who focus on security architecture, product hardening, product security operations, and risk and compliance.
Packsize strives to continuously improve its data privacy compliance. In this effort, the global Packsize organization benchmarks itself against one of the world's strictest data privacy laws: The EU GDPR. As part of its commitment to data privacy, Packsize is supported by an officially appointed Data Protection Officer (DPO) in the EU. To communicate with our data protection officer, please email privacy@packsize.com.
Packsize has a privacy policy published on its website which outlines privacy commitments in accordance with local laws and regulations and is reviewed by management on an annual basis. It can be accessed on our Privacy Policy page.
Onboarding – Background Checks and Training
All potential employees or contractors who will access PackNet systems undergo a criminal background check directed by Human Resources. Packsize employees are required to take and attest to periodic security training.
System administrators and engineers attend more in-depth training that pertains to recommendations of how to best protect against the threats and vulnerabilities in their domain. Packsize team members complete information security and awareness training within 30 days of hire and annually thereafter.
Additional Information
Further information on the security and privacy program for Packsize can be found in PackNet Software Platform GDPR Guidance.
DPS Overview
Overview of DPS
The IoT device Hub Provisioning Service (DPS) is a helper service for the IoT hub that enables zero-touch, just-in-time provisioning to the right IoT hub without requiring human intervention. Reference this Microsoft Wiki for general information around DPS.
Overview of TPM
Trusted Platform Module (TPM) provides hardware-based, security-related functions including:
Generate, store, and limit the use of cryptographic keys
Device authentication by using the TPM's unique RSA key which is burned into the chip
Help ensure platform integrity by taking and storing security measurements of the boot process
Reference this Microsoft Wiki for general information around TPM.
Packsize Implementation of DPS and TPM
Packsize has implemented the DPS to allow for provisioning an IoT edge module to be provisioned to the correct IoT hub once that device is able to connect outbound to the Azure environment.
IoT Acquisition Suppliers provide the public key or endorsement key for the hardware chip for the specific IoT edge module.
The Packsize team registers the public keys to the Azure DPS.
When the IoT image boots up the IoT device will be recognized vie the public key and provisioned to the correct IoT hub.
The IoT edge module will be able to receive jobs.
Whitelisting Requirements
The following ports need to be Whitelisted to allow for Packsize DPS solution to connect to their Azure environment. Reference PackNet Connectivity Requirements [SPEC-00126] for the full list of allow-listing that needs to be enabled for the PackNet Software Platform.
URL | Description | Port |
|---|---|---|
global.azure-devices-provisioning.net | Device Provisioning Service | 443, 5671 |